
KB Technologies Blog
KB Technologies has been serving the Deerfield Beach area since 2002, providing IT Support such as technical helpdesk support, computer support, and consulting to small and medium-sized businesses.
If a Hacker Uses Display Name Spoofing, They Might Look Trustworthy
Business success is often tied to the quality of your business relationships, and there are many people you need to trust: suppliers who can provide you with everything you need, the team who do their jobs, and customers who turn to you because they know they need you. Unfortunately, it is possible for cybercriminals to exploit this trust to achieve their own goals.
"Display name spoofing" is a tactic that many hackers will use in their phishing attacks. When using it, a cybercriminal will pose as someone important to undermine your security by manipulating someone in your business. Let's take a look at what display name spoofing itself is, and how to prevent it from infiltrating your business.
First, let’s break down how display name spoofing works: email signatures are generally overlooked, giving an advantage to cybercriminals. By falsifying the name that appears, the attack becomes even more effective and can do even more damage to your business.
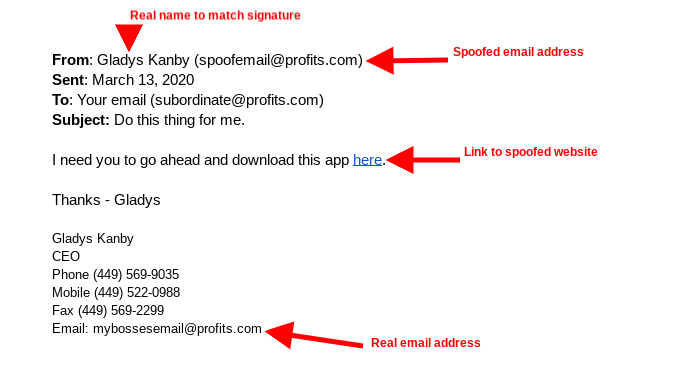
When cybercriminals choose their targets, they look for someone who they might be able to influence and then target them by posing as someone else. If you look closely, one of the most common indicators that an email is not legitimate is the email address itself. Considering that email clients often do not display the full address by default, many employees don’t even consider that something could be questionable or fake.
You should have an access control policy to ensure that your employees can use the resources they need to do their job. You should also put in place similar security measures to protect your digital assets.
Furthermore, you’ll need a strategy that recognizes that your business is exposed to phishing attacks. It is critical that your team is prepared to recognize these attacks and respond accordingly:
- Before you act, check the name and email address of the sender, check the content and check the names of the sender, email addresses, etc.
- Make sure you think twice whenever a sender sends you messages asking for your passwords, login details, email address, phone number or other sensitive information.
- Consider whether the supposed sender would ask you to send your login details by email, or whether they would send you a message at all over other forms of communication.
- If your team members ever doubt the accuracy of an email they receive, they need to be sure to verify it correctly. This usually takes just minutes but can significantly reduce the risk of successful phishing.
These are simple, but effective, ways to better identify cybersecurity threats. In case of the event that your team members should catch one, you should train them to respond appropriately.
For more cybersecurity assistance, make sure you reach out to KB Technologies. Better security solutions and expert assistance is only a call to (954) 834-2800 away.
Tired Of Annoying Computer Problems That Keep Coming Back?
Reach Out Today!
Mobile? Grab this Article!
Tag Cloud
Malware
Users
Efficiency
Computer
Best Practices
Mobile Device
Collaboration
IT Support
Disaster Recovery
Phishing
Data
Technology
Security
Cloud
Productivity
Email
Hardware
Saving Money
Tip of the Week
Hackers
Network Security
Current Events
Business
Innovation
IT Services
Workplace Tips
User Tips
Internet
Cybersecurity
Workplace Strategy
Google
Privacy
Backup
Microsoft
Software
Ransomware
Managed IT Services
Hosted Solutions
Business Computing
Quick Tips
Latest Blog
Managed IT Services: Your Strategic Technology Partner in Boca Raton In an era where technology drives every aspect of business, relying on reactive fixes is like trying to steer a ship by plugging leaks one at a time. At KB Technologies Managed IT in Boca Raton, we offer ma...
Latest News
KB Technologies is proud to announce the launch of our new website at http://www.kb-it.com. The goal of the new website is to make it easier for our existing clients to submit and manage support requests, and provide more information about our services for ...


Comments